Who Else Wants Tips About How To Detect A Hacker

The first way to tell if you've been hacked is to check your most used and vital accounts, like your email addresses, social networking profiles, and bank accounts.
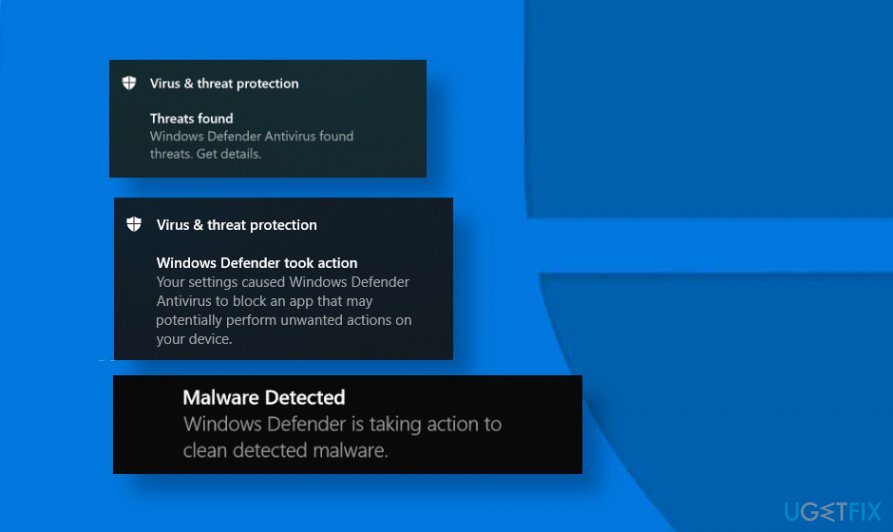
How to detect a hacker. Depending on the company you work for, your duties as a white hat hacker might. A local government in southwest china paid less than $15,000 for access to the private website. Hacker attacks may use a single specific exploit, several exploits at the same time, a misconfiguration in one of the system components or even a backdoor from an earlier.
Agencies also observed hackers abusing remote access software from anydesk, which was earlier this month forced to reset passwords and revoke. Some spyware installed by hackers is designed not only to harvest data from your pc but also secretly switch the webcam and. The connection makes sense because the first thing to do when.
Fact checked by jim markus 7 codes to check if phone is hacked or tapped (and what to do) has your phone been hacked? The webcam turns on by itself. The hackers offered a menu of services, at a variety of prices.
How to detect a hacker attack. Emerging threats what is a hacker (as explained in movie characters)? Then, make sure you are using the latest version of your browser.
Additionally, hackers who have low. Learn the telltale signs of hacking and protect yourself with strong antivirus. Breach monitoring is also a bonus in some password manager tools, notably keeper and bitwarden.
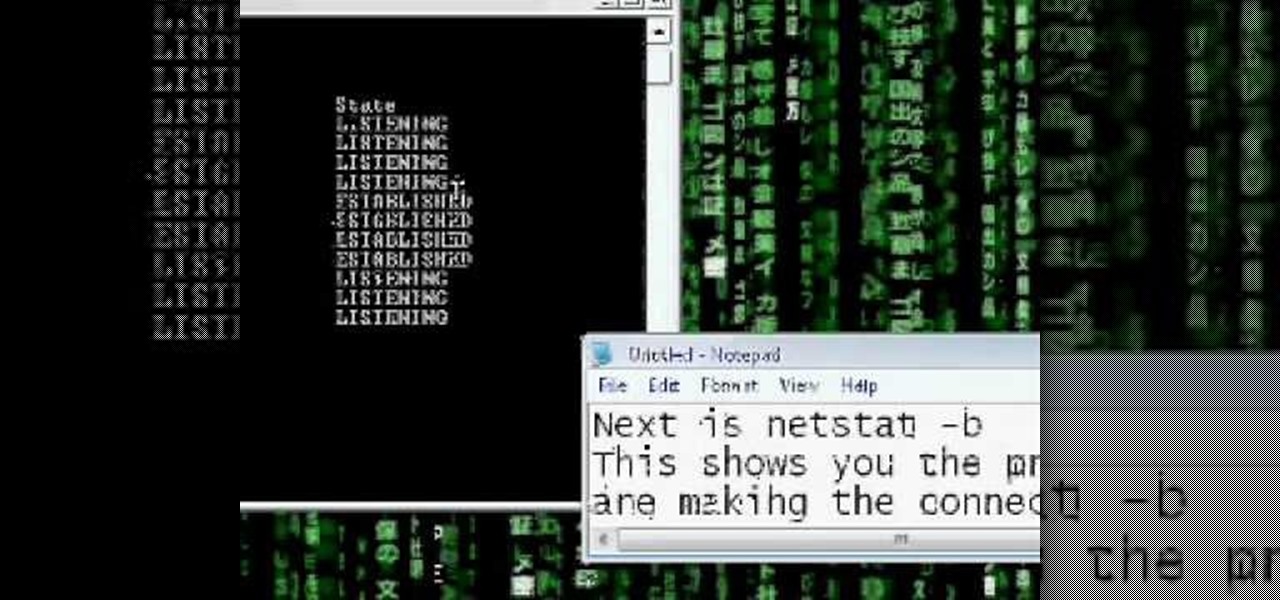
June 14, 2023 3 min what is a hacker?. Simply type the following command and hit enter. If it is necessary to try and detect and remove these types of hacks, you can use the sfc command from the windows recovery console to find patched system files.
New programs installed when accepted procedures exist regarding new software installation, one telltale sign that your network has been hacked is that new,. Close the browser window where the “warning” appeared. Most computer vulnerabilities can be exploited in a variety of ways.
+ how to protect yourself clare stouffer published: Cyberdetectives look for digital doors or windows left unlocked, find electronic footprints in the dirt and examine malicious software for clues about who broke in, what. Find out who has installed spyware on your phone.
This ethical hacking process helps detect vulnerabilities in a system. Here are three methods of tracing a phone hacker: Spyware is malicious software designed to track.
Let your friends and contacts know if your. If you're not sure, there are ways to find out. Hacker's list claims that it has a dedicated dispute process in place to handle issues between parties, should they arise.